Let’s discuss the question: what characteristic describes a vpn. We summarize all relevant answers in section Q&A of website Countrymusicstop.com in category: MMO. See more related questions in the comments below.

Table of Contents
Which characteristic describes a VPN?
What characteristic describes a VPN? It encourages competition and promotes choices.
What characteristics describe IPS?
Explanation: IPS – An intrusion prevention system (IPS) monitors incoming and outgoing traffic looking for malware, network attack signatures, and more. If it recognizes a threat, it can immediately stop it.
What is a VPN and How Does it Work? [Video Explainer]
Images related to the topicWhat is a VPN and How Does it Work? [Video Explainer]
![What Is A Vpn And How Does It Work? [Video Explainer]](https://i.ytimg.com/vi/_wQTRMBAvzg/maxresdefault.jpg)
What service is provided by https?
Allows remote access to network devices and servers. Resolves domain names, such as cisco.com, into IP addresses. Uses encryption to provide secure remote access to network devices and servers.
What is IPS in cybersecurity?
An intrusion prevention system (IPS) is a network security tool (which can be a hardware device or software) that continuously monitors a network for malicious activity and takes action to prevent it, including reporting, blocking, or dropping it, when it does occur.
What are two characteristics of both IPS and IDS sensors choose two?
Explanation: IDS sensors work off line and are passive. They add very little latency, however they cannot stop trigger packets. An IPS can stop trigger packets but because they are installed inline they add some latency and jitter to the traffic.
What can IDS detect?
An intrusion detection system (IDS) is a device or software application that monitors a network for malicious activity or policy violations. Any malicious activity or violation is typically reported or collected centrally using a security information and event management system.
What service is provided by pop3?
Retrieves email from the server by downloading the email to the local mail application of the client. Allows remote access to network devices and servers. Uses encryption to provide secure remote access to network devices and servers.
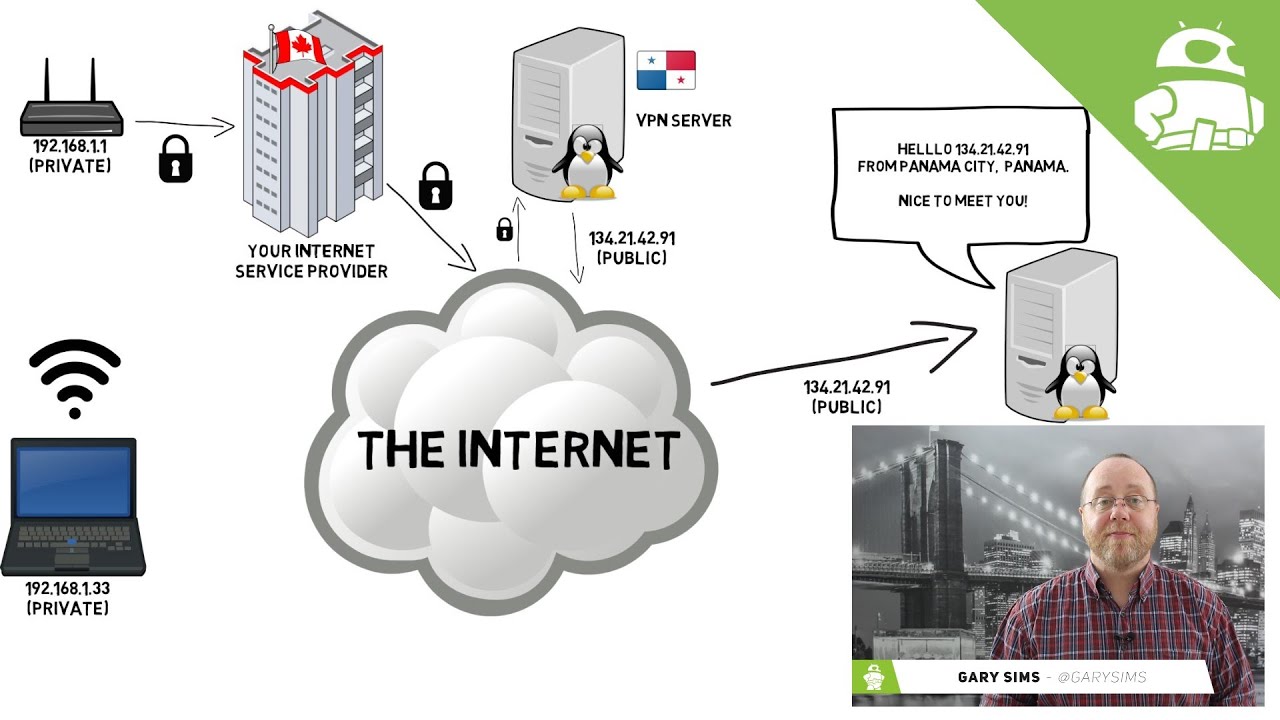
What is a VPN? – Gary explains
Images related to the topicWhat is a VPN? – Gary explains
What protocol can be used for encryption between a Web browser and a Web server?
Hypertext transfer protocol secure (HTTPS) is the secure version of HTTP, which is the primary protocol used to send data between a web browser and a website. HTTPS is encrypted in order to increase security of data transfer.
What service is provided by https CCNA?
Allows remote access to network devices and servers. Resolves domain names, such as cisco.com, into IP addresses. Uses encryption to provide secure remote access to network devices and servers.
Can IPS prevent DDoS?
Typical IPS devices also claim some anti- DDoS protection. While it is true they can (and do) incorporate some basic protection, the majority of current IPS products evolved from software-based solutions that were signature-based.
Is a firewall an IPS?
The main difference being that firewall performs actions such as blocking and filtering of traffic while an IPS/IDS detects and alert a system administrator or prevent the attack as per configuration. A firewall allows traffic based on a set of rules configured.
Does Palo Alto have IPS?
Palo Alto Networks differs from traditional Intrusion Prevention Systems (IPS) by bringing together vulnerability protection, network anti-malware and anti-spyware into one service that scans all traffic for threats – all ports, protocols and encrypted traffic.
What is a characteristic of an IDS?
Characteristics of a Good Intrusion Detection System. An intrusion detection system should address the following issues, regardless of what mechanism it is based on: It must run continually without human supervision. The system must be reliable enough to allow it to run in the background of the system being observed.
What are VPNs?
Images related to the topicWhat are VPNs?

What are two shared characteristics of the IDS and the IPS?
Both analyze copies of network traffic. Both use signatures to detect malicious traffic. Both rely on an additional network device to respond to malicious traffic.
What is an advantage of using an IPS?
The IPS offers zero-day threat protection, mitigates brute force password attempts, and provides protection against availability threats, such as DDoS and DoS attempts.
Related searches
- itn version 7 00 itnv7 final exam
- Match the type of threat with the cause not all options are used
- ITN version 7.00 itnv7 final Exam
- match a statement to the related network model not all options are used
- Match a statement to the related network model Not all options are used
- what are the two characteristics of public cloud
- what statement describes a vpn
- match the characteristic to the forwarding method not all options are used
- what are three commonly followed standards for constructing and installing cabling choose three
- match the application protocols to the correct transport protocols
- characteristic of a vpn
- which two traffic types use the real time transport protocol rtp choose two
- match the type of threat with the cause not all options are used
- Match the application protocols to the correct transport protocols
- Which two traffic types use the Real-Time Transport Protocol (RTP)? (Choose two)
- Why would a Layer 2 switch need an IP address
- why would a layer 2 switch need an ip address
Information related to the topic what characteristic describes a vpn
Here are the search results of the thread what characteristic describes a vpn from Bing. You can read more if you want.
You have just come across an article on the topic what characteristic describes a vpn. If you found this article useful, please share it. Thank you very much.
